Exploring API Inventory  ¶
¶
As soon as the API Discovery module has built the catalog of your endpoints (your API inventory), you can explore it in the API Discovery section of Wallarm Console. Learn from this article how to go through the discovered data.
Endpoints¶
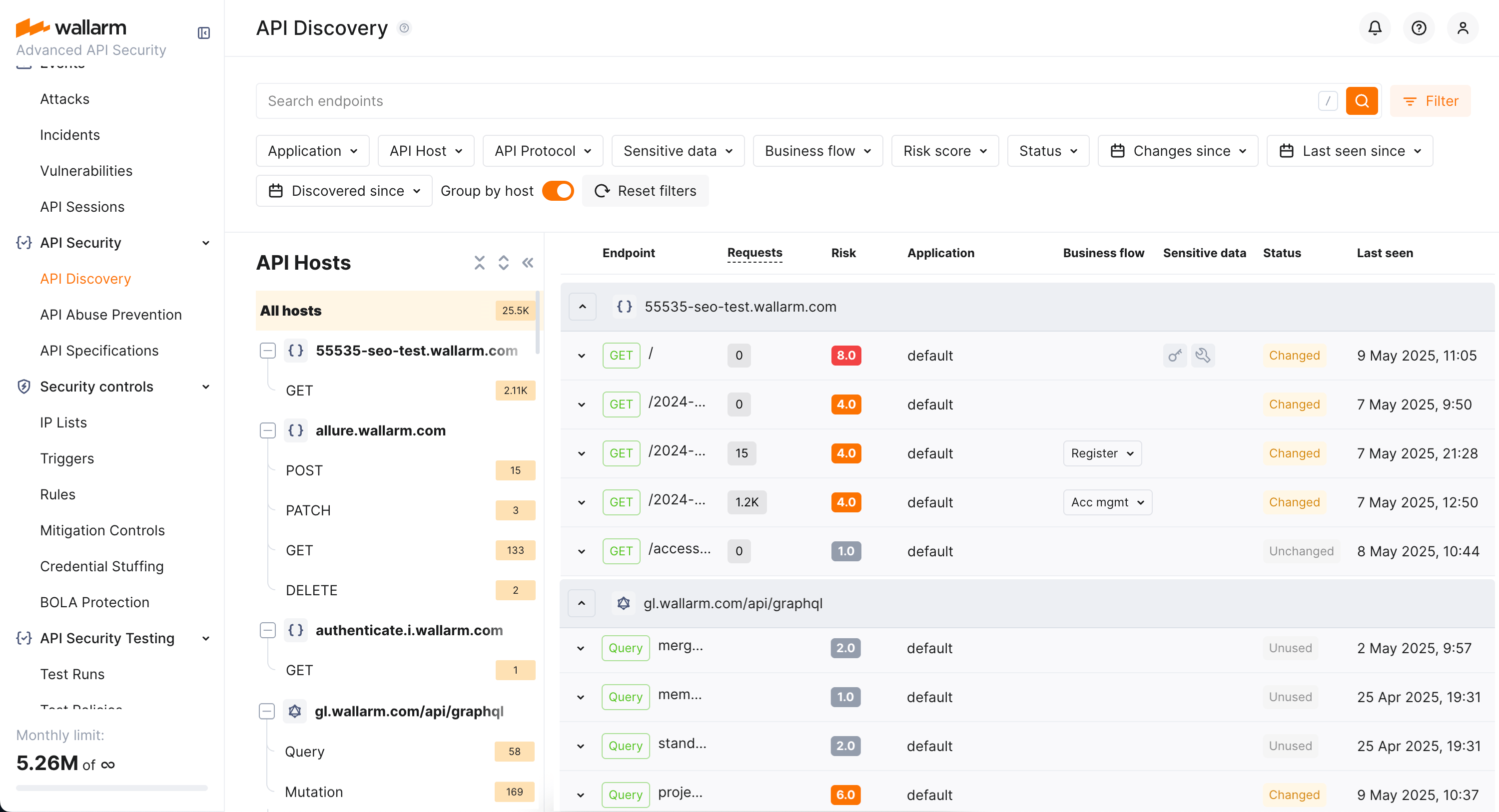
Explore your discovered API inventory using the API Discovery section in the US or EU Cloud.
By default, endpoints and operations are sorted by host/endpoint or operation name. Also, Group by host is on. With grouping by host disabled, you can sort endpoints by risk.
Filtering¶
Among a wide range of API endpoint filters, you can choose the ones corresponding to your analysis purpose, e.g.:
-
Find the endpoints characterized with the highest risk level to analyze and mitigate the risks.
-
Find endpoints related to specific application.
-
Find the endpoints that have been changed or newly discovered in the last week and that process PII data. This kind of request can help you to stay up to date with critical changes in your APIs.
-
Find the endpoints being used to upload data to your server by the PUT or POST calls (REST) or mutations (GraphQL) (API protocols filter with methods for REST and operation types for Graph QL). Since such endpoints are a frequent attack target, they should be well secured. Using this kind of request you can check that endpoints are known to the team and are well secured from attacks.
-
Find the endpoints processing sensitive data to ensure they are properly secured.
-
Find the endpoints of a deprecated API version (e.g. by searching
/v1) and make sure that they are not used by clients.
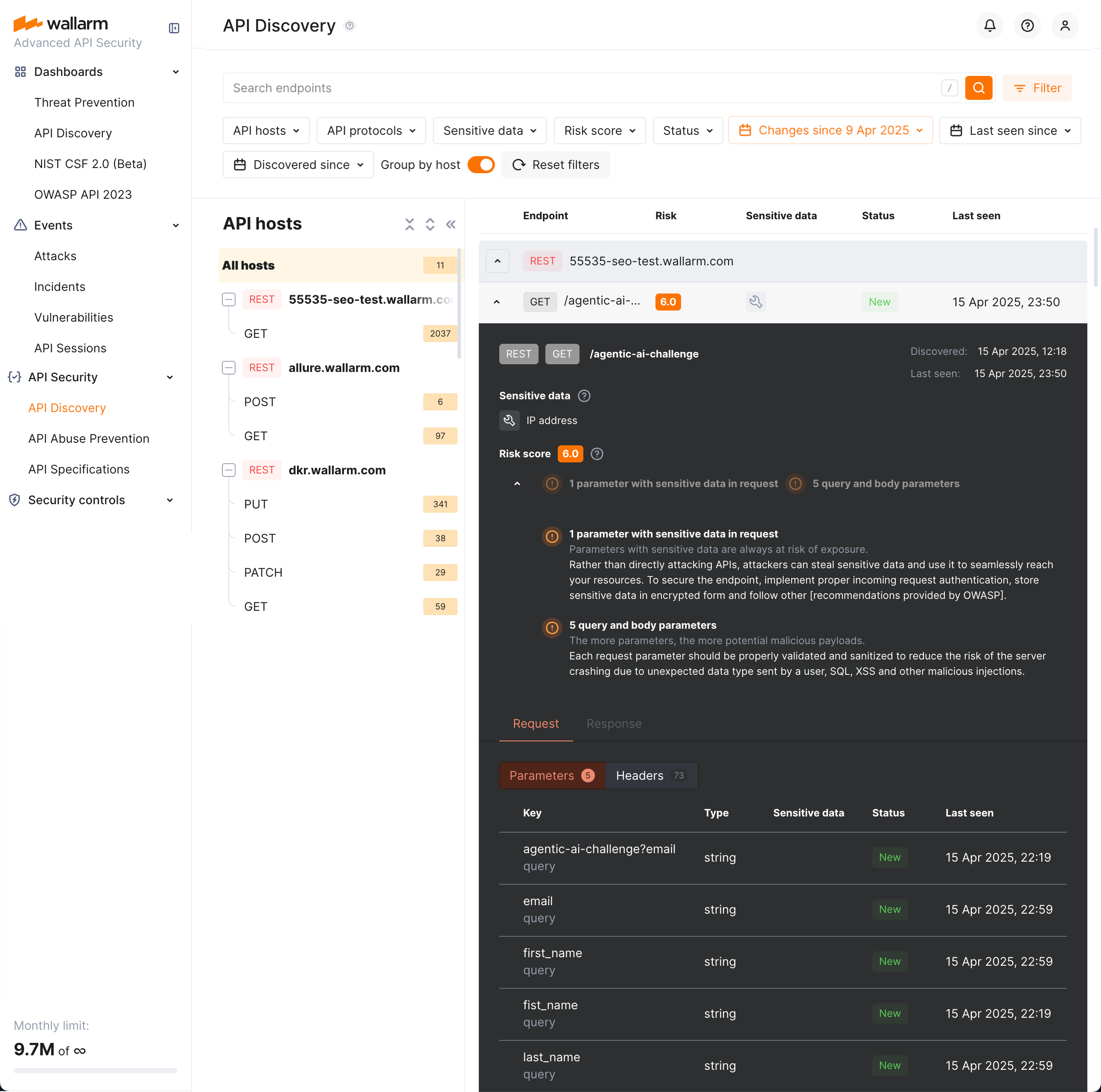
REST endpoint details¶
By clicking the REST endpoint, you can find its details, including transferred sensitive data, risk score and what contributes to it, headers and parameters of requests and responses:
Each request/response parameter information includes:
-
Parameter name and the part of request/response this parameter belongs to
-
Information about parameter changes (new, unused)
-
Presence and type of sensitive data transmitted by this parameter, including:
- Technical data like IP and MAC addresses
- Login credentials like secret keys and passwords
- Financial data like bank card numbers
- Medical data like medical license number
- Personally identifiable information (PII) like full name, passport number or SSN
-
Type/format of data sent in this parameter
-
Date and time when parameter value was last transferred by requests
Format and data type¶
In REST endpoint details, in the Type column for parameters of request and responses, Wallarm indicates the data format identified through traffic analysis or, if not specific, a general data type.
For REST endpoints, Wallarm attempts to detect various data formats such as Int32, Int64, Float, Double, Datetime, IPv4/IPv6, among others. If a value does not conform to any recognized data format, Wallarm classifies it under a general data type, such as Integer, Number, String, or Boolean.
This data allows checking that values of the expected format are passed in each parameter. Inconsistencies can be the result of an attack or a scan of your API, for example:
-
The
Stringvalues are passed to the field withIP -
The
Doublevalues are passed to the field where there should be a value no more thanInt32
Variability¶
URLs can include diverse elements, such as ID of user, like:
-
/api/articles/author/author-a-0001 -
/api/articles/author/author-a-1401 -
/api/articles/author/author-b-1401
The API Discovery module unifies such elements into the {parameter_X} format in the endpoint paths, so for the example above you will not have 3 endpoints, but instead there will be one:
/api/articles/author/{parameter_1}
Click the endpoint to expand its parameters and view which type was automatically detected for the diverse parameter.
Note that the algorithm analyzes the new traffic. If at some moment you see addresses, that should be unified but this did not happen yet, give it a time. As soon as more data arrives, the system will unify endpoints matching the newly found pattern with the appropriate amount of matching addresses.
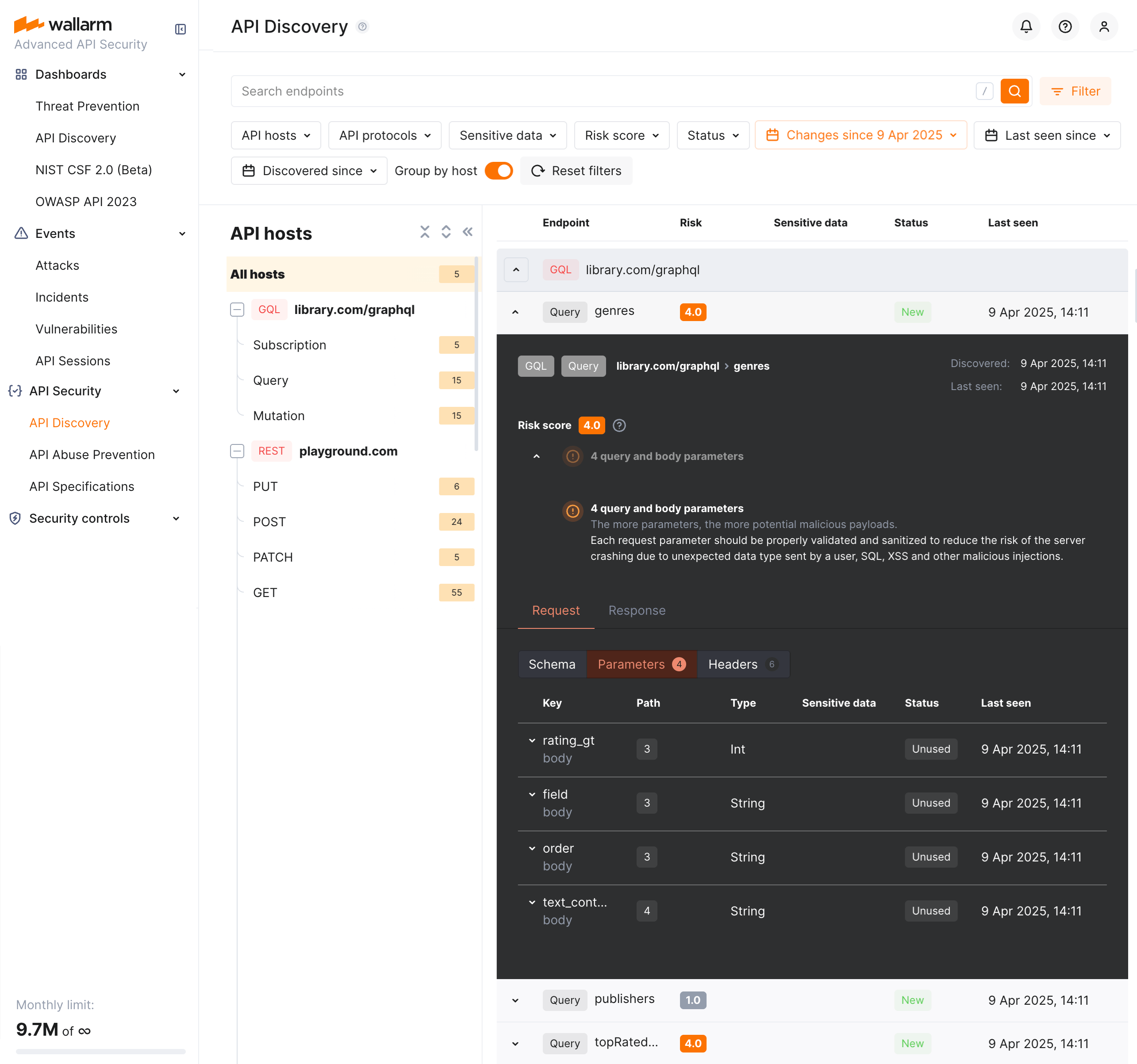
GraphQL operation details¶
By clicking the GraphQL operation, you can find its details, including transferred sensitive data, risk score and what contributes to it, schema, parameters and headers of requests and responses:
Each request/response parameter information includes:
-
Parameter name and the part of request/response this parameter belongs to
-
Path: the hierarchical location of a parameter within a GraphQL query structure
-
Information about parameter changes (new, unused)
-
Presence and type of sensitive data transmitted by this parameter, including:
-
Date and time when parameter value was last transferred by requests
Format and data type¶
In GraphQL operation details, in the Type column for parameters and headers, Wallarm indicates the data format identified through traffic analysis.
For GraphQL operations, data formats are detected in accordance with the scalar types specification:
-
Int: A signed 32‐bit integer. -
Float: A signed double-precision floating-point value. -
String: A UTF‐8 character sequence. -
Boolean: true or false.
Endpoint activities¶
The number of requests related to the endpoint is displayed in the Requests column. Click this number to open the API Sessions section with the list of user sessions for the last week with these requests.
Within each found session, only requests to your endpoint will be initially displayed - in session, remove filter by endpoint to see all requests for context.
A structured view of session activity helps in understanding your endpoint place in malicious and legitimate activities, its relation to sensitive business flows and required protection measures.
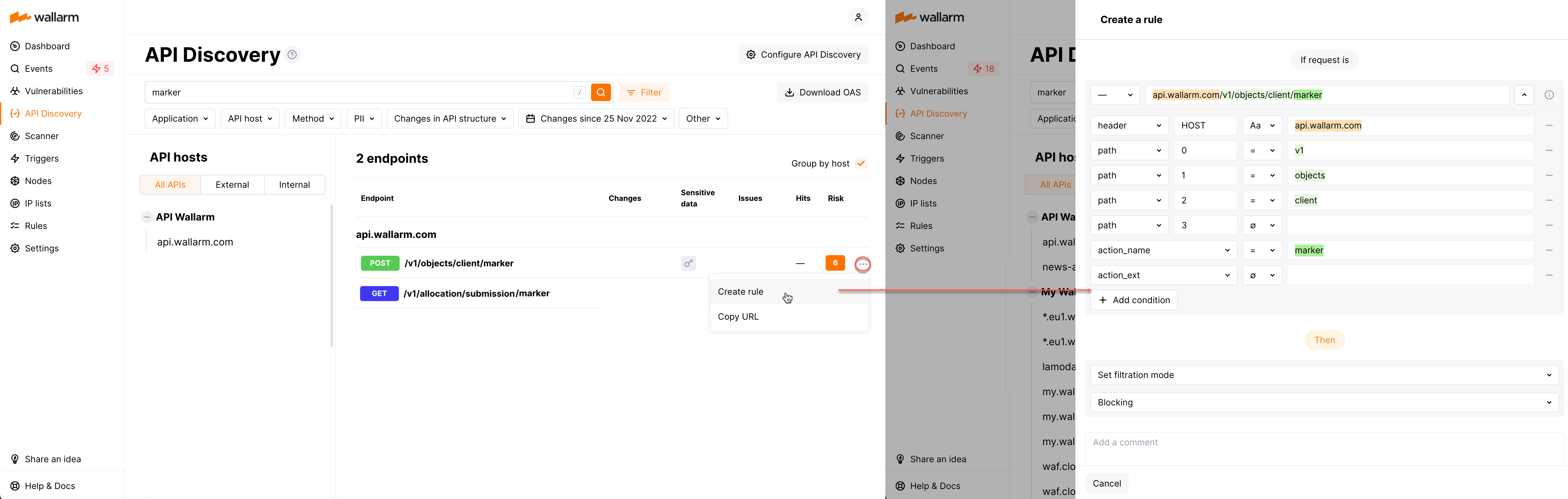
Creating rules for API endpoints¶
You can quickly create a new custom rule from any endpoint of API inventory:
-
In this endpoint menu select Create rule. The create rule window is displayed. The endpoint address is parsed into the window automatically.
-
In the create rule window, specify rule information and then click Create.